Update (9/20/09): This post is slightly out-of-date now, if you’re looking for instructions on how to use Espionage with Time Machine, the best place to look is in the backup section of its manual. Espionage’s manual is accessible online *and* within Espionage itself.
This topic is covered extensively in the Help documentation that comes with Espionage, but from the amount of email I’m getting it appears it deserves a blog post as well.
While designing Espionage, I realized that its ability to intercept any access to folders could lead to problems with backup applications, since it would be quite annoying to the user if the password prompt appeared any time say, when Time Machine tried to backup their folder.
For this reason Espionage was given an ignorelist. Now whenever Espionage detected that an application on the ignore list was trying to access one of its protected folders, it would automatically allow or deny that application access without prompting the user (depending on whether the application was “whitlisted” or “blacklisted”, respectively).
By default Espionage has rules for Spotlight, AppleFileServer, and Time Machine. You can add other applications to the ignore list either by adding them manually in the preferences, or directly from the password prompt. Here’s what the ignore list looks like with SuperDuper! whitelisted:
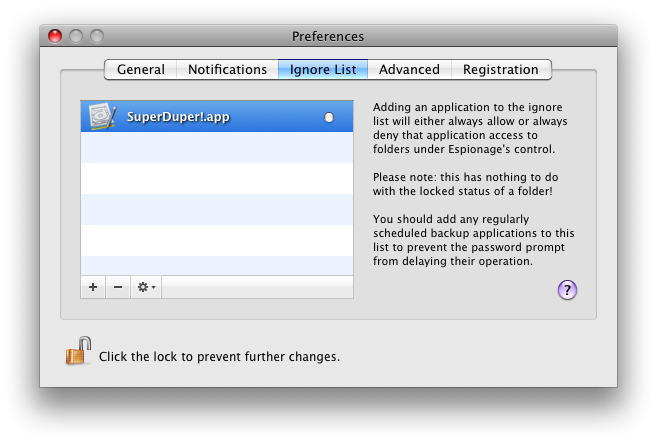
Keep in mind, however, that when “granting an application access” to the folder does not actually mean it can read the contents of that “folder.” This gets us into the hairy details of how Espionage works.
When a folder is encrypted by Espionage, it takes the contents of that folder puts it into a sparse disk image*. This disk image will be named “.<foldername>.sparseimage”, and is placed into the folder. The original folder, meanwhile, is placed into the Trash where the user can back it up, securely delete it using the Finder, or do whatever they please with it. When the folder is unlocked, the disk image is moved into the parent folder, is mounted in a special location, and a link is created in place of the folder pointing to that mount.
Thus, when you backup an encrypted folder, you’re really backing up an encrypted disk image.
Currently, restoring from a backup to an *unlocked* state will confuse Espionage, but your data will still be safe, just hidden. We’ll be releasing a maintenance build very soon to address this issue and some others. I suspect that this situation is rare enough though that we’ll fix the problem before anyone runs into it. If, between now and the next release you do end up having to restore from a backup that has a folder in the unlocked state and run into problems, just contact support and we’ll help you out in a jiff!
Also, because we’re currently using sparse disk images, making a change to the folder’s contents will cause Time Machine to backup the entire folder. Yes, we realize this is annoying for those of you using Time Machine, and you can expect sparsebundle support to come soon to solve this problem.
* Note: If the folder is less than 2048 MB (or whatever the value of “Minimum Image Capacity” is), the capacity will be set to that, otherwise the capacity will be 10x the folder size. You can edit the default capacity, as well as the default filesystem of disk images from the Advanced preferences. Look for major improvements related to this in a future release…
This may be a silly question, but here goes.
What if something goes wrong, and even though I enter the correct password Espionage doesn’t open the file? Could a software bug or data corruption cause me to lose my data? In other words, should a regular spreadsheet file become corrupted, I might still be able to recover all or most of the data. But what about encrypted data that then becomes corrupted?
Hey Peter,
That’s a very good question actually! A software bug in Espionage shouldn’t ever make you unable to access your data, because ultimately that data is stored in an encrypted disk image, which is just hidden. You can always unhide the disk image and open it manually with your password to access your data.
As for corruption, the same corruption problems and solutions that affect your hard drive affect disk images. For this reason you should maintain regular backups.