EDIT February 17, 2016: 3.6.4 and 3.6.5 release notes included here as there are only minor changes.
We’re momentarily back from our break in cryptocurrency-research-land (where we’ve been advancing our goal of sustainably open-sourcing Espionage) to bring you the immediate release of Espionage 3.6.3!
“But wait! This doesn’t seem like such an exciting release! What is this business about dropping support for three operating systems? Are you trying to screw us over?! Bad Tao Effect, bad!”
*ahem*
Our dear customers, we love you, we only want what’s best for you, and we will never try to screw you over. ^_^
10.7, 10.8, and 10.9 Are All Insecure. Stop Using Them.
Although we will keep Espionage 3.6.2 available for download here, we strongly recommend that all users upgrade to at least 10.10 (preferably 10.11), and here’s why:
Problem #1: Internet connections are not secure on 10.7 and 10.8
While investigating a serious vulnerability in Sparkle (the software update framework Espionage uses), we discovered that Sparkle did not work at all on our 10.7 test machine.
It turns out that neither Mac OS 10.7 nor 10.8 are capable of handling secure SSL/TLS connections! TLS is the protocol behind the S in HTTPS, and it’s responsible for securing almost all Internet connections.
Versions of TLS prior to 1.2 are afflicted by a serious vulnerability, making the lock icon in your web browser even less meaningful than it already is. It seemed silly to support these insecure systems when they can’t even load Espionage’s homepage (because it only allows TLSv1.2).
Well known infosec researcher Adam Langley had this to say:
This seems like a good moment to reiterate that everything less than TLS 1.2 with an AEAD cipher suite is cryptographically broken.
Problem #2: 10.7, 10.8, and 10.9 are all vulnerable to root privileges escalation
Your Mac has various user accounts on it besides the one you use, and the most powerful of these accounts is called root. Up until 10.11, this account could do anything (and even in 10.11 it can do almost anything). It can delete anything and install anything, including key loggers that would break Espionage’s protection.
Normally it is not possible for a program to gain these “root powers” (privileges) unless you, the user, manually type in your admin password. However, sometimes a bug is discovered that will allow a program running under any account to gain these privileges without any intervention from the user. This is extremely dangerous, and this will forever be the reality all the way up to Mac OS 10.9.
Combine Problem #1 with Problem #2 and you have a recipe for total disaster. Therefore we want to do everything we can to discourage the use of these insecure operating systems, especially given that our customers want security.
The #1 thing users can do to keep themselves secure is keeping their software up-to-date.
Sparklegate
Speaking of keeping software up-to-date, Espionage 3.6.3 includes an updated version of Sparkle, the popular OS X software-update framework.
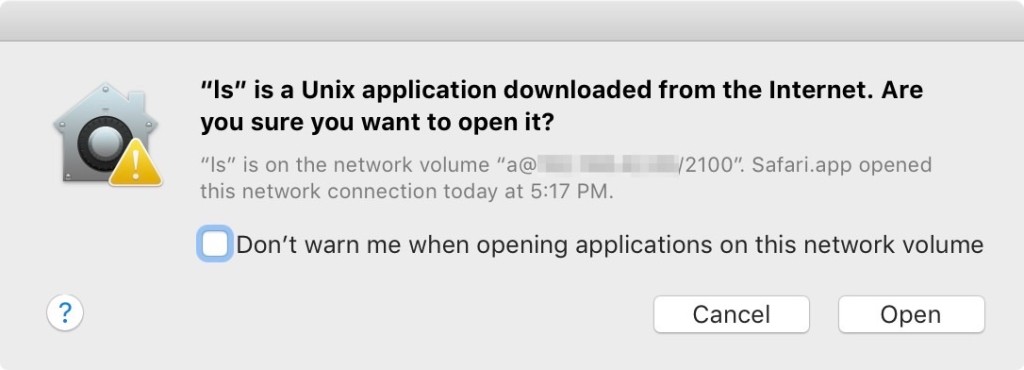
Sparkle had a vulnerability that made it possible for anyone on your network (a malicious attacker) to execute arbitrary code on your machine.
This problem is mitigated somewhat for apps that use HTTPS to check for updates (as Espionage does), but it is still a serious problem, especially on OS X 10.7 – 10.8 because HTTPS is broken on those operating systems (as described above), and even then it’s still possible (though rare) for someone to compromise HTTPS for TLSv1.2 (the latest version).
So just to be on the safe side we’ve updated Espionage’s version of Sparkle and we’ve dropped support for all the compromised operating systems that Apple is no longer updating.
However, you still most likely have compromised apps, so read this:
Sparkle is a very commonly used framework. Almost every app you have that you did not get from the App Store will be using it, and this vulnerability is ultimately due to a fundamental flaw in OS X, so there may be other affected other apps out there.
Until Apple fixes this flaw, we recommend taking these steps to protect your Mac.
We strongly recommend that all users use the latest version of OS X.
OS 10.11 El Capitan is great. Apple did a good job of addressing many of the performance and stability issues that were plaguing 10.10, and since it’s a free upgrade you really don’t have much of an excuse for not using it. Especially if you want to keep your Mac safe and secure.
Release Notes
Here’s what’s new in our minor version update:
- Security
- Improved Plausible Deniability by quietly mounting folders (hides some Console messages)
- Updated Sparkle (even though we use HTTPS) just to be on the safe side due to a vulnerability.
- Improvements!
- Use HTTPS for newsletter registration during setup.
- Bug fixes
- (3.6.4) Fixed “error decrypting database” on 10.10 (introduced in 3.6.3).
- (3.6.5) Fixed Sparkle checking for updates too frequently (thanks Sabri!)
- Misc.
- Dropped support for 10.7, 10.8, and 10.9 because all of these operating systems are insecure (details in blog release notes for this version).
The signature for Espionage.dmg is here and also here (pubkey here). The SHA256 of the main binary is also noted below.
Enjoy! 😀

$ openssl dgst -sha256 Espionage.app/Contents/MacOS/Espionage
SHA256(Espionage.app/Contents/MacOS/Espionage)= 36bc10690789acea932f57f1d6b485247e92194dc2a79ad6f66dd6fbd1fd334d
P.S. Espionage 3.6.2 will still remain available for download here for those who insist on playing Russian Roulette with their security.