This post comes straight out of Espionage’s built-in help.
Before Espionage came onto the scene, it was very difficult to securely protect individual folders. The ability to put a password on a folder wasn’t even possible. Because of Espionage, this has all changed.
The typical method of protecting data on Mac OS X has been the use of “vaults”, which are really just encrypted files called disk images that are mounted in a specific location.
Disk images have many limitations. While they allow you to securely protect data, they are difficult to use, and can’t be used to seamlessly protect application data on an individual basis, that is, until now.
Some applications have tried to make disk images easier to use by referring to them as “vaults” and giving you a “one-click” method for creating them. But the problem with this approach is that you still have to use a separate application to manage the vault, and you can’t use it to protect important application data (like email).
Apple’s FileVault has a single vault that does protect application data, but it does this by encrypting your entire home folder. This “all or nothing” approach can slow down your computer and drain battery life because the process of encryption is expensive.
Your home folder has a lot of data stored inside of it. Application data, movies, music, etc. Most of it doesn’t need encryption. Accessing this data, without encryption, is slow enough already because of the slow speed of hard disks, so why make it over 3x slower unnecessarily?
Espionage to the Rescue!
So we thought, “Why not simply have encrypted folders?”
That would solve all of those problems! Espionage lets you encrypt only the data that you want encrypted, and makes it easy to manage your encrypted data by doing all of the dirty work for you!
You don’t have to worry about disk images, or “vaults”. Just drag a folder onto Espionage and it takes care of the rest. From then on you can simply double-click on that folder and a password prompt will appear asking for that folder’s password. Once you’re done using the data that’s inside of
it, just right-click on it and select “Lock” from the menu to lock it. And protecting application data has never been easier.
Benchmarks
Encrypting data comes at the price of reduced performance when accessing that data. This is because the process of encryption and decryption results in data being passed through complex algorithms that transform the data into unreadable and readable states, respectively. Running these algorithms takes time, and makes the CPU work harder, all of which can impact performance (and battery life for laptop users) when accessing that data.
This is why Espionage gives you fine-grained control over what gets encrypted. 🙂
OK, but how much?
To answer this question we ran the standard suite of benchmarks using Intech’s QuickBench software with default settings on a Macbook Pro laptop with the following specifications:
| CPU: | 2.2 GHz Intel Core 2 Duo |
| HDD: | Seagate Momentus 200 GB 7200 RPM |
| RAM: | 4 GB |
We ran benchmarks on the hard drive, and two mounted disk images (the same system that FileVault uses). Each disk image was a sparse disk image formatted with a 500 MB capacity and HFS+J filesystem, the only difference being the encryption strength.
The results were rather dramatic, with more than a 3x difference between sequential operations for AES-128 and almost a 4x difference with AES-256:
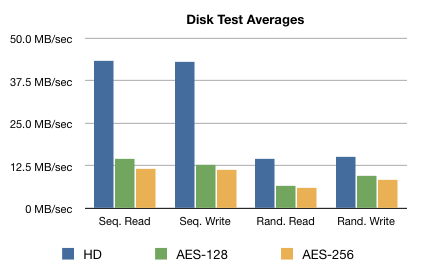
Layman’s definitions for what each of these tests mean are at the bottom of this document.
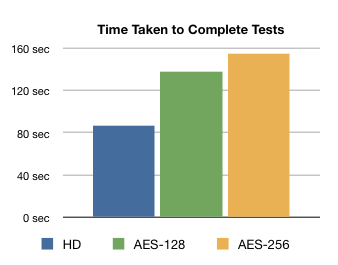
The time taken to complete the standard suite of benchmarks was measured using a stopwatch.
To give an indication of how accessing encrypted data can impact battery life, we measured how idle the CPU was during the first 70 seconds of the benchmarks (higher is better):
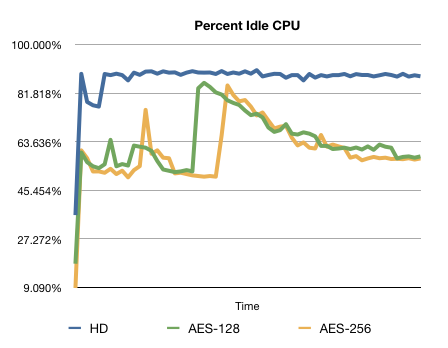
All running applications were terminated (except for important system tasks) and the internet connection was turned off during the tests.
| Layman’s Definitions and Examples | |
| Sequential read: | How quickly data can be read in order. Operations such as opening files and watching movies typically result in sequential reads. |
| Sequential write: | How quickly data can be written in order. Operations such as copying and duplicating files typically result in sequential writes. |
| Random read: | How quickly data can be randomly read. Launching applications can result in this sort of activity. |
| Random write: | How quickly data can be written to random parts of the hard drive. Databases can result in this kind of activity. |
| Idle CPU: | The percentage of the CPU that’s not being used. |