What are "unencrypted password protected folders"?
Simply put, they are folders that Espionage "puts a password on" but does not actually modify (i.e. through encryption).
Whenever there is an attempt to open such a folder, Espionage will present a password prompt requesting a password for that folder. If the wrong password is entered, Espionage will deny access to that folder.
However, it's fairly simple to get past this password prompt.
If the folder is encrypted, however, the contents are still safe. Here is what an attacker would see inside of an encrypted folder:
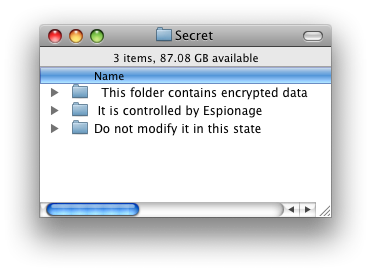
This folder contains a hidden disk image that contains the real folder contents, which are safe because they are inaccessible without the right password.
If the folder was not encrypted, however, you would be able to see its contents after disabling Espionage's helper program.
Why have unencrypted protected folders at all then?
There are some situations in which putting a password on a folder, but not encrypting it, might be desirable, and for this reason we allow this possibility.
For example, some users might have a large collection of videos that they don't want their technically challenged parents having access to, but don't care enough about to encrypt since encrypting data can take a while and slow down their computer.
Technical Discussion: Why not run EspionageHelper as root?
It is true that one way to "fix" this problem is to make EspionageHelper run as root, then a regular user wouldn't be able to kill it. We chose not to do go this route for two main reasons:
- You can still access the folder's contents when EspionageHelper is not running, for example, by booting from another drive and mounting the hard drive that contains the folder.
- Running it as root could make the system vulternable to various exploits. EspionageHelper uses many of Apple's frameworks that Apple does not guarantee are safe to load in root processes (and recommends against doing so).
If you want your data to be secure, use encryption.